In this article, you will learn about web application security and the options within Scriptcase that can help you protect your applications.
Enhancing the security of a web application is a fundamental concern; the global nature of the internet exposes web applications and APIs to attacks from various locations and at different levels of scale and complexity. As such, web application security encompasses a variety of strategies and covers many parts of the software supply chain.
Security in web applications also plays a crucial role in compliance with LGPD, ensuring that user data is handled securely and by legal requirements for privacy and data protection.
The General Data Protection Law (LGPD) is a Brazilian legislation aimed at protecting the privacy of citizens’ data. Approved in 2018 and inspired by the European Union’s General Data Protection Regulation (GDPR), LGPD establishes rules and guidelines for organizations to collect, store, process, and share personal data in the public and private sectors.
Some key points of LGPD include:
Data subject consent, purpose, adequacy and necessity principles, transparency and information, data security, data subject rights, responsibility, and accountability.
Non-compliance with LGPD can result in significant penalties, including administrative fines, warnings, data blocking, and even partial or total prohibition of activities related to the processing of personal data. Therefore, organizations dealing with personal data in Brazil must comply with LGPD requirements to protect data subject rights and avoid adverse legal consequences.
“Privacy by Design” and “Privacy by Default” are two fundamental principles in privacy and personal data protection, especially in designing and developing systems, products, and services.
Privacy by Design focuses on integrating privacy considerations from the beginning of the design process of systems, products, or services. In other words, the idea is that privacy should not be just an afterthought or an addition after the central development has been completed but should be incorporated from the early design stage.
The Privacy by Design approach emphasizes the importance of anticipating and addressing privacy issues during all development lifecycle phases, from conception to implementation and ongoing maintenance. This may include adopting practices such as data minimization, encryption, access control, transparency, and other measures to protect users’ privacy.
Privacy by Default focuses on the default setting of systems, products, or services to ensure maximum privacy protection for users without requiring additional actions. This means that by default, settings should be as privacy-enhancing as possible. Users can then make adjustments if they wish to relax these settings to meet their individual preferences, but privacy protection should be the initial configuration.
For example, an application may have its privacy settings set to collect only the minimum data necessary for its basic functionality, with the option for users to enable more permissive settings if they wish to share more information.
In summary, while “Privacy by Design” emphasizes the integration of privacy considerations in all stages of design and development, “Privacy by Default” focuses on ensuring that privacy protection is the initial and standard configuration of systems, products, and services. Both principles are crucial to ensuring adequate protection of users’ privacy.
What are the common security risks of web applications, and how can Scriptcase help implement solutions for each?
Scriptcase is a low-code platform for developing database-driven web applications. All development is done directly in the browser, using a visual interface and automatic code generation tools. Source code is automatically generated in PHP and JavaScript and runs independently of the tool.
Regarding security, like any other software development platform, the security of the final application depends on various factors, including the developer’s expertise, proper implementation of security practices, and server configuration where the application will be hosted, among others.
Scriptcase is designed with features to help developers create secure applications, such as user authentication, access control, and input data sanitization. However, the security of the final application also depends on how the developer uses and configures these resources.
Web applications can face various attacks, depending on the attacker’s objectives, the nature of the targeted organization’s work, and specific application security gaps, especially when cyber attacks are increasingly common.
Here are some measures that can be taken to increase the security of a web application with the help of Scriptcase.
1 – Proper Authorization:
Implementation of an access control system to ensure that users have access only to the areas and functionalities of the application that are appropriate for their roles.
Scriptcase provides an automatic security module that protects the system by creating an access control and defining user privileges, ensuring that only authorized users can access specific applications.
Five types of security modules are available, which function similarly; their main distinction lies in how permissions are applied to users.
Check out the security types:
- Security Module by Group – System usage permissions are assigned to user groups, and each user must belong to at least one of these groups.
- Application Security Module – Access permissions to system applications are individually assigned to each system user.
- User Security Module – There is no access privilege; all users with system access will have access to all applications.
- LDAP Security Module – Authentication Only – Performs simple user authentication, similar to what is seen in the User Security Module.
- LDAP Security Module – Total Control – Access privileges not assigned to groups, as in the Group Security Module, are applied in this type of security.
Watch this video for a presentation of the Scriptcase security module.
2 – Robust Authentication: Use secure authentication methods, such as two-factor authentication (2FA) or multi-factor authentication (MFA), to ensure that only authorized users can access the application.
The security module automatically implements two-factor authentication with Email, SMS, or Google Authenticator options.
Watch this video to learn more about this option.
3 – Login Attempt Limit: Implement account lockout policies or timing out after a specific number of unsuccessful login attempts to mitigate brute force attacks.
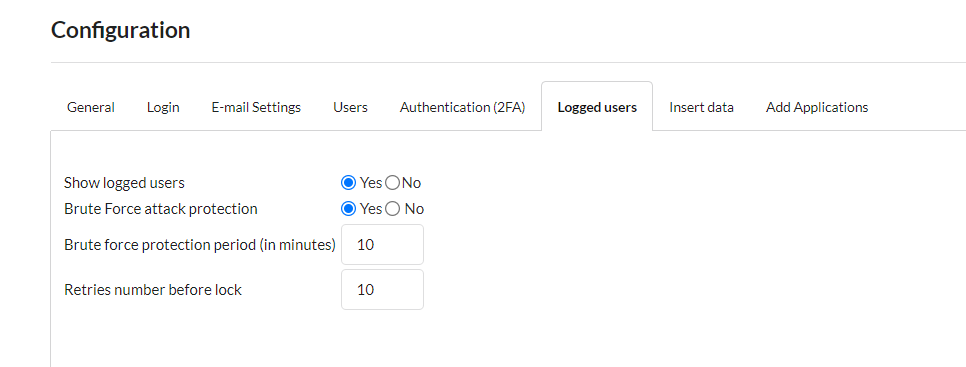
In the Scriptcase security module, there is an option to enable protection against brute force attacks. The developer can allow it to and set a lockout time and a number of login attempts.
Captcha and Recaptcha: Implementing a security measure known as challenge-response authentication. CAPTCHA protects against spam and password decryption with a simple test that proves you are a human, not a computer attempting to breach a password-protected account. reCAPTCHA is a tool used via API provided by Google to perform form submission verifications, adding security during form confirmation (preventing automation for submission).
Within the Scriptcase security module, the developer can add Captcha and Recaptcha by simply enabling an option. Scriptcase automatically implements these options on the login screen; for Recaptcha, Google API data is required.
Watch this video for an example of implementing Google’s Recaptcha.
4 – Protection against SQL Injection: Use parameterized queries or prepared statements to prevent SQL injection attacks.
In Scriptcase, there are native macros to protect fields/variables against SQL injection. Therefore, all database accesses generated by Scriptcase are protected.
Prevention of Cross-Site Scripting (XSS): Sanitize and validate all user inputs to prevent malicious scripts from being injected and executed in the user’s browser.
HttpOnly – These are cookies that the server can set or JavaScript but cannot be accessed by JavaScript in any way.
With the HTTPOnly parameter enabled, stealing sessions via XSS is significantly hindered as JavaScript cannot read the content of these cookies. A widely exploited XSS attack is stealing user session cookies. The theft of cookies is performed through a JavaScript command that sends the cookies to an external URL where the attacking user has control.
This option is enabled by default in all Scriptcase applications.
Prevention of Cross-Site Request Forgery (CSRF): Implement CSRF tokens to protect against CSRF attacks, ensuring that all requests originate from the application, not malicious sources.
With this option activated, Scriptcase prevents a malicious attack on a page where unauthorized commands are transmitted by a user whom the page trusts. It validates protection against known attacks such as “Cross-Site Request Forgery.” Prevent direct calls by URL Enable username and password.
Security Headers: Security headers are a layer of protection to prevent cyberattacks on web pages. An example is HTTP headers, which protect user data or prevent the insertion of malicious scripts into pages.
Hearders

Data Encryption: Use encryption to protect sensitive data, both in transit (using HTTPS) and at rest (using robust encryption algorithms).
Scriptcase also enables encryption macro options, which return the field or variable encrypted.
Ex. 1: Encrypting a local variable:
$encrypted_field = sc_encode({my_field});
Ex. 2: Encrypting a user variable:
$encrypted_field = sc_encode($my_variable);
Regular Updates: Keep all application components (operating system, web servers, libraries, frameworks, etc.) up to date with the latest security patches.
Scriptcase sends regular updates to its clients, periodically updating its libraries and APIs. This applies to both the development and production environments.
Audit and Monitoring: Implement audit logs to track suspicious activities and continuously monitor the application for anomalous behaviors that may indicate a potential attack.
In Scriptcase, in addition to the security module that can deploy a log table, there is a logging module where the developer can record events and activities in the system, creating a detailed history of user actions such as logins, data updates, and other relevant operations. Logs help monitor user changes in the system and contribute to auditing cases.
The logging module allows for the creation of various log schemes. Each application in the project can be linked to a log scheme, which will be configured individually. Each project can contain one or more log schemes.
Employee Training: Educate developers and end-users about security best practices, such as using strong passwords, identifying phishing emails, and emphasizing the importance of data security.
Regular Security Testing: Conduct regular penetration tests and security assessments to identify and fix vulnerabilities before attackers can exploit them.
It is a low-code development environment used worldwide by over 50,000 developers and has been in the market for over 20 years.
Regular Data Backup: Maintain regular backups of application data and store it securely in off-site locations to ensure recovery in the event of a security compromise.
Scriptcase has a backup system that allows the user to make a complete backup of created projects. We recommend that backups are made regularly. It is also possible to version projects.
Watch the two videos below to learn more about these two options.
– Project Backup
– Versioning
Conclusion
Implementing these security practices can significantly reduce the risk of a web application being compromised by cyberattacks. However, it’s important to remember that security is an ongoing process and that new threats and vulnerabilities may emerge over time, requiring a proactive approach to maintain application security.
Therefore, to ensure the security of an application developed with Scriptcase, developers must adopt best security practices, such as protection against SQL injection, Cross-Site Scripting (XSS), robust authentication and authorization, and input data validation. Additionally, it’s crucial to keep Scriptcase and any other libraries or frameworks used updated, as updates often include security fixes to address known vulnerabilities.
In summary, if used correctly, Scriptcase can be a secure tool, with secure development practices and regular updates to ensure protection against potential vulnerabilities.
Watch this video to complement the post:
Follow our blog and stay up to date with our latest content.

You might also like…